How to build a fully encrypted NAS on OpenBSD
In this article I will try to give you all the clues on how to build yourself a fully encrypted NAS for your home network. But first of all, why?
Well, I believe that my data is my data and not somebody elses. I’m not paranoia nor a pirate but having all my personal data in my network encrypted gives me a peace of mind. I mean, in a time where there are some private(!) organizations who think they can tell you/me/everybody what they should and shouldn’t do, it’s time to take some precautions, that’s all. Like I said, it’s about a peace of mind and of course, because we can. ^_^
The end-result will be:

my personal encrypted fileserver
click to enlarge
a server running on OpenBSD with a filesystem on software RAID, so we can handle a disk which decides to stop working all together (and this machine emails you when a drive fails). On top of that we’ll have a fully encrypted filesystem which will take care of on-the-fly encryption and decryption of your files, the data you copy to the server gets encrypted and the data you read from it gets decrypted, all on-the-fly… ^_^ This data than can be presented to your network by Samba, NFS, FTP, you name it.
If, in some crazy world, some organization would believe they can invade my home and take my stuff, there’s not much to be found except gigabytes of ones and zeroes. ^_^
Well, of course, I already built something similar over two years ago. But there has been one flaw in that one. Even though we don’t like anyone accessing our data except ourselves and those we trust, we do like to have some data-security and not lose anything if a drive fails, right? So in fact this is an update to that earlier project. (and yes, I got to this after a drive failed…)
Now when you investigate the wonderful world of RAID, you’ll see that there are fantastic RAID-controllers available, with the possibility of connecting up to 24 drives which can be presented to the operating system of choice as one big drive. But, with SATA-disks now available of 1 terabyte and soon more, you must be in need of a lot of data if you can’t hold it onto one drive. In this how-to we’re not going to make things complicated by building arrays of a multitude drives. We’re going to use two drives in mirror and with disks available today, that could give you an array of 1TB (mine is 320GB by the way).
On top of that one array, we’re going to build an encrypted filesystem of roughly the same size of one such a disk (so, in theory that could also be 1TB). The machine is capable of encrypting and decrypting on-the-fly. Better put, you won’t notice a thing of the whole process. On my personal system I can read and write with average speeds of around 20MB/sec (which is faster than your average laptopdisk without encryption).
To make it totally clear, there’s no problem if you want to run more than one RAID-array or more than one encrypted filesystem. You can have up to 4 encrypted filesystems (and even more if you recompile the kernel).
Why is it now called a NAS?
Well, NAS is one of these magical abbreviations that pops up all over the place. Everything that can store something and connect to a network is called a NAS nowadays. According to that loosely definition, you could even call your average cellphone a NAS... it can store something and connect to a network (and then I’m referring to the internet, not the cellphone network).
Anyway, to tighten it a little down, I guess we can follow the definition on Wikipedia:
NAS systems usually contain one or more hard disks, often arranged into logical, redundant storage containers or RAIDs (redundant arrays of independent disks), as do traditional file servers. NAS removes the responsibility of file serving from other servers on the network and can be deployed via commercial embedded units or via standard computers running NAS software.
But it also says:
It should be noted that NAS is effectively a server in itself, with all major components of a typical PC – a CPU, motherboard, RAM, etc. – and its reliability is a function of how well it is designed internally.
So, because we have RAID and it serves files to the network, I guess we can call it NAS. It does fulfill everything a typical NAS does, but because we’re using OpenBSD and not some trimmed down version of some OS (no offence to those projects though) we also keep the opportunity open to have this fully configurable *nix-box in our network do a lot more than just serve some files (for instance, download some torrents). When you think of it, the size of a typical OpenBSD install
(sans GUI) is about the size what’s considered acceptable as an embedded OS. Well, imho there’s no need to strip it down, it is lean as it is (especially compared to non-*nix OSes ^_~) and this way we keep a lot of options open for future add-ons.
If you do like a stripped down OS for your NAS, I recommend you take a look at FreeNAS or when you’re just looking for having some encryption in your network, I suggest you take a look at CryptoBox.
Well, to be totally honest with you, this how-to is meant for people who like the left picture bettter than the right… (I actually like them both, on the left you can see the controls of my TV and on the right the controls of one of my amplifiers... ^_^)
So, in short, this how-to is meant for people who’d like to have a fully configurable box in their network and who know what they’re doing.
I’ll only cover how you can make software RAID with an encrypted filesystem on top. I won’t cover the installation of OpenBSD itself or the installation/configuration of the fileserving services like Samba/NFS etcetera.
Anyway, here we go:
The prerequisites:
I assume you have a fair understanding of the Unix Command Line Interface. Next to that you need to familiarize yourself with OpenBSD (if you haven’t already done so) and the installation thereof. There’s an excellent Installation Guide on the OpenBSD-site. My box now runs OpenBSD 4.0, but this will also work on, say, 3.8 to 4.1.
From there you should be able to follow my how-to. I’ve put the actual how-to on a separate page which you can find here:
hardware requirements
Well, a lot of hardware will go actually. You’ll need a motherboard to which you can connect three hard drives and a fairly decent CPU for the encrypting/decrypting. For the encryption, I’ve used an MP1800+ before and that gave me around 8MB/sec. Nowadays I use an Opteron 146 (2.0GHz) and that gives me around 20MB/sec (25MB/sec read, 16MB/sec write). So if you take anything which is not too old (AMD64s are great for this purpose imho), you’ll be fine.
To give you an idea, this is my setup which gives me around 20MB/sec throughput:
Chieftec 4U-case
Asus SK8N
AMD Opteron 146 (2.0GHz)
512MB Reg ECC PC2700
Intel Pro1000 gigabit NIC
2MB PCI-videocard…
Adaptec 2940 SCSI-card
Seagate Barracuda 9LP ST39173W 9GB boot/OS-disk
2x Seagate Barracude 7200.10 320GB in RAID1, datadisks
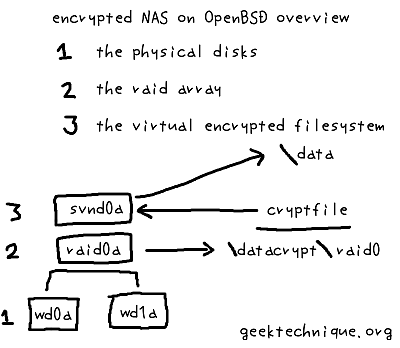
an overview of everything we do in the how-to
click to enlarge
the actual how-to:
OpenBSD encrypted NAS HOWTO
After this and after we configured the file serving services we’d like (which I don’t cover in this how-to) we’ll have one big encrypted filevault and to show you that it indeed is a NAS presenting itself to different OSes, here are some screenshots from the clients I use (all connecting through Samba btw):
top left: Nautilus on Ubuntu (my workstation)
top right: OS X on my powerbook
bottom left: Windows explorer on Vista (my media center)
bottom right: Inside Media Center.
Bonus

encrypted USB drives connected to the encrypted NAS
click to enlarge
And then there’s the possibility of adding USB-drives to this setup as well! Actually, you can build an encrypted filesystem on everything that can hold a file ^_^ (don’t you just love this? ^_^). After you mount a USB-drive, you can follow the same procedure from filling a file with zeroes or /dev/prandom on…
Now, from a personal experience (I’ve been using encryption on my fileserver for over two years now and I added RAID about 8 months ago) this truly gives a peace of mind. The reason I’ve written it down was because I was forced into refamiliarizing myself again with all this after a power outage in my home. Because the machine did an unclean shutdown, I had work to do and while I was at it, I though I just as easily could write it all down. Now in the original how-to to which this is an update, I also added a bittorrent webinterface and I’m still using that also. Because the machine now is totally current again, I guess I could look into revising that part too… If I get some results there, you can expect a follow-up to this how-to.
good luck to everyone who tries this.
the actual how-to:
OpenBSD encrypted NAS HOWTO
related:
...making an encrypted fileserver
OpenBSD encrypted fileserver HOWTO
Putting OpenBSD/AMD64 on my fileserver _
RAID on my OpenBSD fileserver
encrypted storage server… getting there…
DIY trackback:
slashdot
openbsd.org – press ^_^
net-security
G.C.U. (french)
astalavista
BSD news
del.icio.us (at a certain point it was very hot!)
hackaday
you can find all of my projects overhere







Love the blog, I always keep up to date on it, and when I saw this I was really interested, however it would have been really cool to see an in-depth how-to covering everything from the right hardware to choose to installing the software, to setting up the RAID/encryption. It is cool to get a glimpse into what you’re running, but it would be so awesome if I could try to build something just like this, especially considering I have some decent hardware laying around (Athlon 64 3500+, 1GB RAM) that I could put to good use.
Also, what are the benefits to doing something like this on OpenBSD rather than a Server oriented linux distro like Ubuntu Server?
Well, the setting up the RAID/encryption is covered in the actual how-to. I’m not sure if that’s the case but I can understand someone misses that (I just added some extra links) ;-)
About going in-depth on all the other subjects. Somehow I’d love to, but that is going to be massive and I do have a lot of other work/projects that need finishing also, I’m sorry about that. I guess I'm covering the part that sets it apart from all the other NAS/fileserver-how-tos
About the hardware, well, as simple as it sounds, with nowadays hardware this will run on just about anything. Of course, if you really want this to be of some grade, I’d suggest you take some server-grade hardware, but if you or whoever has a spare motherboard with a considerably fast CPU (let’s say Athlon XP or AMD64, Pentium4 etcetera), you’re good to go. My choice is running this with a separate OS-disk, so in total that gives you three disks. One for the OS and two identical big disks for the file-serving part. (I also added some text about the hardware)
About the choice for OpenBSD. Well, because of my earlier project, I’m running my fileserver on OpenBSD for quite some time now and I don’t have a reason to switch that. Stuff like this can be done on linux too, but I leave it to others to write up how-tos for that ;-)
Ahh, I hadn’t seen the original HOW-TO, thanks for the quick response and advice. Another question, would it be possible to mix interfaces (ex: IDE and SATA hard drives) and have the NAS function just as well? Thanks.
Oh yeah, you could, although I really wouldn’t know how a RAID-mirror is going to perform if you mix interfaces and/or drives. I’d recommend two big identical drives on an identical interface. Although, get this, even when you buy new gear from a big boy like HP, you could end up with drives who carry the same (HP) partnumber but are in fact from different manufacturers (for instance, Seagate and Maxtor) and going by their configurators and such, two of those drives could very easily end up in the same RAID-array…
Anyway, back to the subject, for the RAID-mirror you need two ‘devices’ of the same size but you can make those out of anything you have laying around (and then use the smallest size of the two) and for the encryption you need one ‘device’ on which you can store one big file (as big as the drive/raid-array), that’s all. How you connect it on the back-end is up to you and/or the stuff you have laying around.
About putting identical drives into a RAID array… Bad idea! ;)
HP actually makes a wise move when mixing all sorts of manufacturers into the RAID arrays they deliver.
The reason for this is a probabilistic one. The probability of identical drives failing at the same time is actually quite high, making the redundancy a hypothetical one.
If you absolutely have to stick to one manufacturer, at least make sure you don’t buy drives all from the same production month.
Even if only one of the identical drives fails, the intense reconstruction process of rebuilding the array might kill the other one.
To cut a long story short: The drives in the array should only have the size and the interface in common, manufacturers and ages should not be identical.
We get a lot of HP disk shelves and we’ve always got a set of disks from the same manufacturer with them, so I’m not sure where you get that from. If you are going to use non-identical disks in a RAID set, it’s not the size in bytes but the number of sectors and sector size which is important. (PS this image verification sucks. I’m on my third attempt now.)
> so I’m not sure where you get that from.
Well, everything you order at one and the same moment probably will always come with identical disks. I’ve experienced myself though that I ordered two extra disks (15k 74GB SCSI U320 68-pin) with the same HP-number but I got two boxes, with each containing a drive of different makes… (a Maxtor and a Seagate)
> Also, what are the benefits to doing something like this on OpenBSD
> rather than a Server oriented linux distro like Ubuntu Server?
not getting pwned?
> Also, what are the benefits to doing something like this on OpenBSD
> rather than a Server oriented linux distro like Ubuntu Server?
Apart from the fact that Linux is only one step less dumbed down than the other commercial alternative.
I like the “pr0n” folder.
Always remember: The internet is for pr0n.
Really nice guide.
I’m dying to ask though, why the Cisco 2600? What is it for?
>why the Cisco 2600? What is it for?
Well, I’m somehow always experimenting with routing and routers. At this moment, this old Cisco 2600 with dual ethernet is my router at home. With an OpenBSD-bridge in front and after it ;-)
It’s positioned like this, because there’s a fan underneath it and this way it can get some air. I would really need some 19” rackspace at home at some point but somehow I’m reluctant to go that way, because once I have that, I’m probably triggered to get even more 19” gear and well, where to stop from there? ;-)
In case you move around far from your NAS :) then you might find this system useful http://dynebolic.org as it provides easy encryption for your home on usb stick.
some details are here http://tazebao.dyne.org/privacy
thanks for this howto! openbsd rocks :)
Very nice! I have several places that I can use this sort of thing. Banks tend to be very picky about data encryption on drives, and we need various ways of doing things depending on the situation. Thanks for the info!
:)
what is running (bottom right:) Inside Media Center?
DEAR SIR,
We are dealers in computer electronics,we would like to purchase from you the following Seagate Barracuda 7200 80 GB 3.5 in SATA .we need 800 pieces could you please send us a
quotation with the best prices by cif Entebbe airport.waiting to hear from you soon.
Regards
mugerwa
MUMJI COMPUTER ELECTRONICS
PLOT 35 DASTER STREET
TELEFAX 256414258243
KAMPALA-UGANDA.
This gives you a false sense of security. If the authorities, on behalf of whatever corporation they’re supporting, break down your door and seize your equipment, they’re also going to threaten you with prison, huge fines, and legal fees if you refuse to turn over the encryption key. Are you prepared to go to prison and be broke for the rest of your life in order to protect your pr0n?
A better strategy would be to financially support organizations like the EFF who are actually fighting the recording cartels and the government in court.
Encryption is good against thieves and hackers. Preemptive lawsuits are the only defense against tyranny and corporate greed.